Removing Offline Domain Controller from Active Directory
We see this one a lot: a domain controller that either crashed or was uncleanly demoted, but never removed from the Active Directory forest. In this scenario, the domain controller is gone for good, but the remaining domain controllers are still attempting to replicate with the offline server.
Aside from the replication errors that will fill the event logs of the remaining, functional, domain controllers, this situation can cause authentication and DNS lookup failures for members of the domain. Since the original domain controller is gone, we'll need to manually remove it from Active Directory.
Instructions
Seize FSMO Roles
Before we start cleaning up, we need to make sure that the offline domain controller was not holding the Flexible Single Master Operation (FSMO) roles.
-
Run
netdom query fsmoon a working domain controller in the forest.netdom query fsmo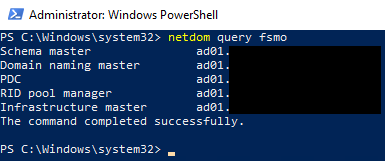
-
If the non-functional domain controller was holding the FSMO roles, we need to seize, or force-transfer, them to a working domain controller. If the FSMO roles are held on a working domain controller in the forest, you can move on to the next section.
Before seizing FSMO roles, you must be absolutely sure that the domain controller currently holding the FSMO roles is never coming back online. Once the roles have been seized, the old domain controller should not be reconnected to the network, even if it has been restored or recovered.
-
Use the
Move-ADDirectoryServerOperationMasterRolecmdlet to transfer the roles to a working domain controller. We add the -Force parameter to seize the roles.Move-ADDirectoryServerOperationMasterRole ` -Identity <TargetDC> ` -OperationMasterRole ` DomainNamingMaster, ` InfrastructureMaster, ` PDCEmulator, ` RIDMaster, ` SchemaMaster ` -Force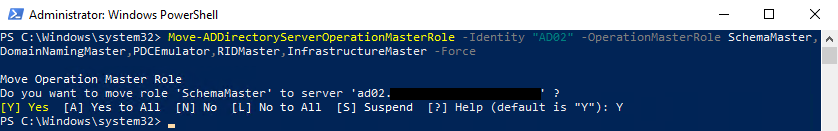
If you receive an "Access Denied" or similar permission error when running
Move-ADDirectoryServerOperationMasterRole, ensure that your user is a member the Enterprise Admins and Schema Admins group and that you are running PowerShell as Administrator.
-
Remove DC from Users and Computers
-
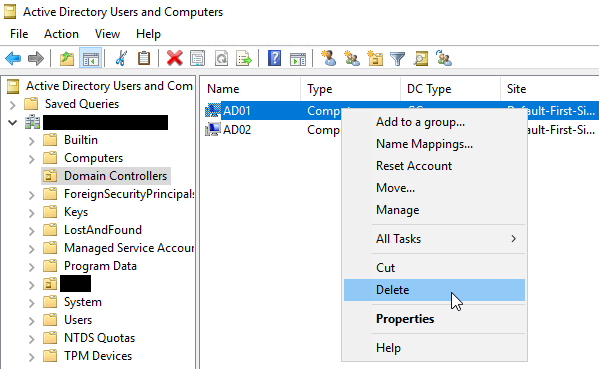
From a working DC in the forest, open Active Directory Users and Computers, navigate to the Domain Controllers container, right-click on the non-functional domain controller and click Delete.
-
Click the Yes button to confirm deletion.
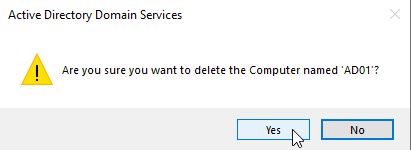
-
The next prompt warns that you should remove a domain controller using the Remove Roles and Features Wizard. Since this is not an option in our case, we select Delete this Domain Controller anyway. It is permanently offline and can no longer be removed using the removal wizard. and click Delete.
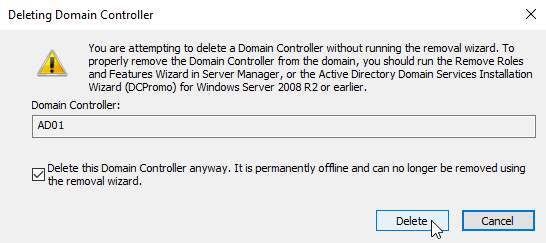
Remove DC from Sites and Services
-
From a working DC in the forest, open Active Directory Sites and Services, expand the site where the non-functional domain controller was located.
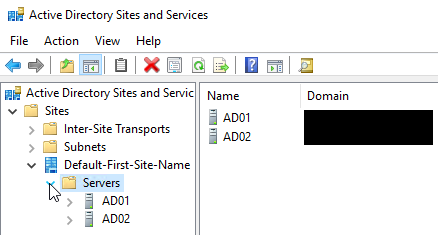
-
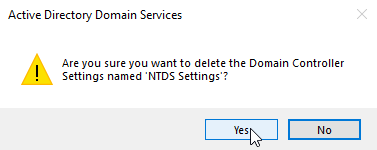
Expand the non-functional domain controller, right click on NTDS Settings, and choose Delete.
If NTDS Settings is not listed under the non-functional domain controller, it was probably deleted when the domain controller was removed from Active Directory Users and Computers. In that case, move on to Step 5.
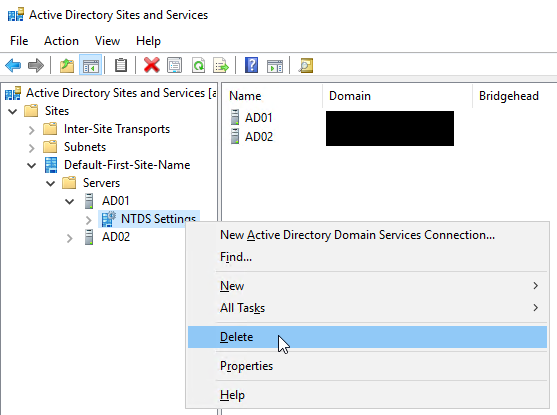
-
Click Yes to confirm deletion.
-
The next prompt warns that you should remove a domain controller using the Remove Roles and Features Wizard. Since this is not an option in our case, we select Delete this Domain Controller anyway. It is permanently offline and can no longer be removed using the removal wizard. and click Delete.

-
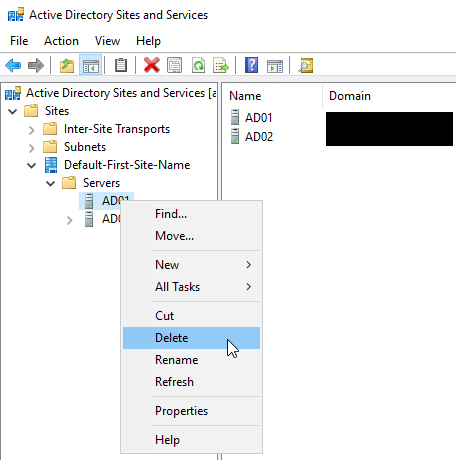
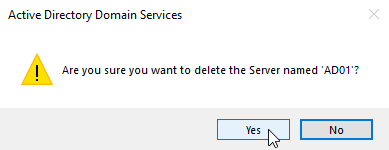
Right-click on the non-functional domain controller and choose Delete.
-
Click Yes to confirm deletion.
DNS Cleanup
Now that the offline domain controller has been removed, we need to manually delete any DNS records that reference it.
Removing the wrong DNS entries can result in replication errors in your domain, so please take care when performing DNS cleanup tasks. If the wrong records are deleted by mistake, the Netlogon service will attempt to recreate missing records upon restart.
-
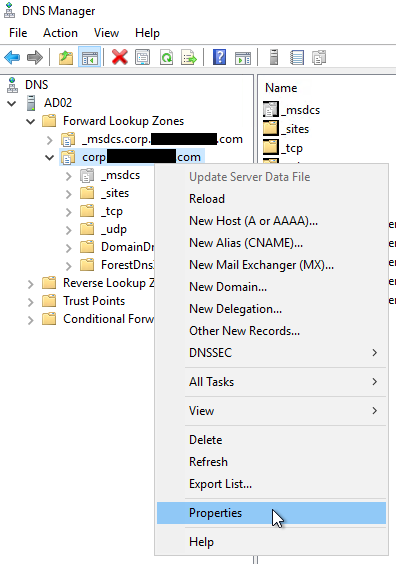
From a working DC in the forest, open DNS Manager, right-click on the forward lookup zone for your domain, and click Properties.
-
Under the Name Servers tab, select the FQDN of the domain controller that was removed, click Remove, then click OK.
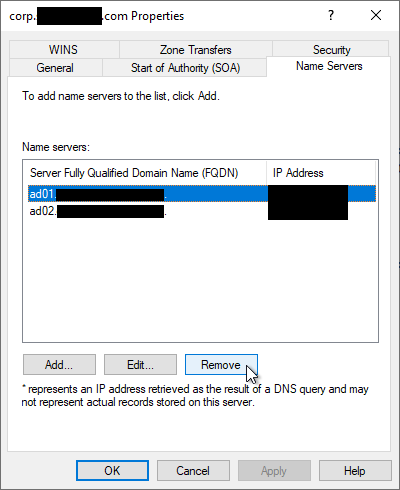
-
Repeat steps 1 and 2 for the _msdcs forward lookup zone as well as any reverse lookup zones in your domain.
-
Expand the forward lookup zone for your domain, right-click on the static A record for the domain controller that was removed, and click Delete.
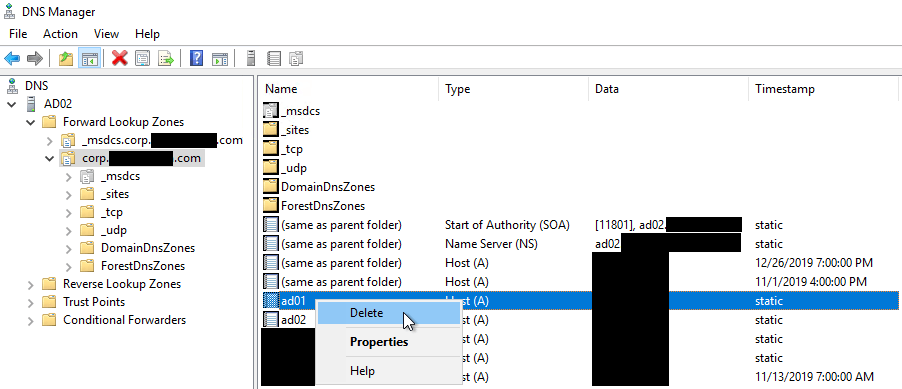
-
Delete the reverse lookup PTR record for the domain controller that was removed.
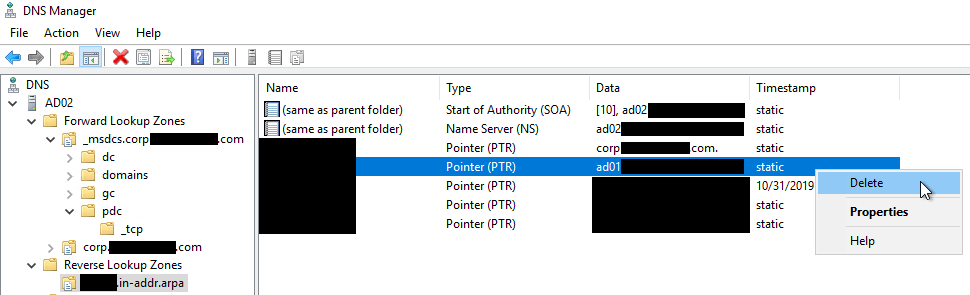
-
Under the _msdcs forward lookup zone, right-click on the CNAME pointing to the domain controller that was removed, and click Delete.
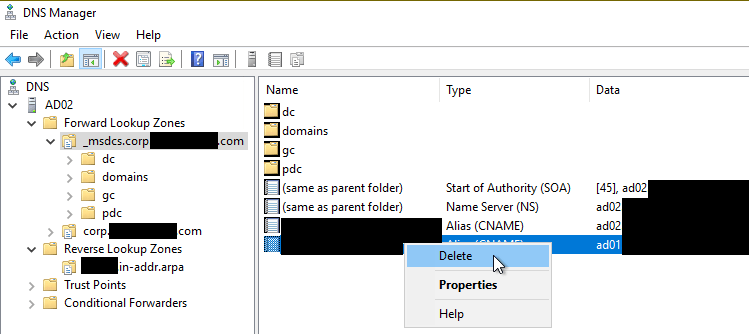
-
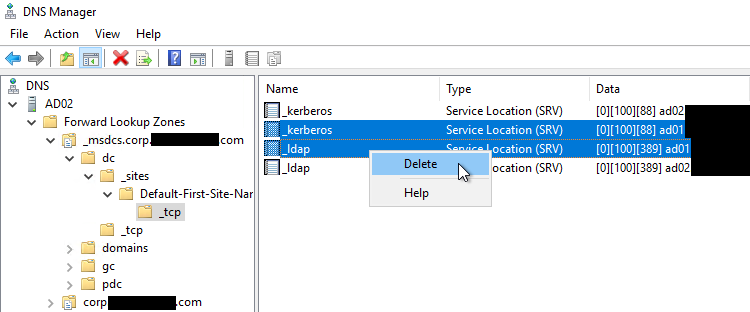
Under the forward lookup zone for your domain, expand the _sites, _tcp, and _udp folders, and their sub-folders, and delete any SRV records that point to the domain controller that was removed.
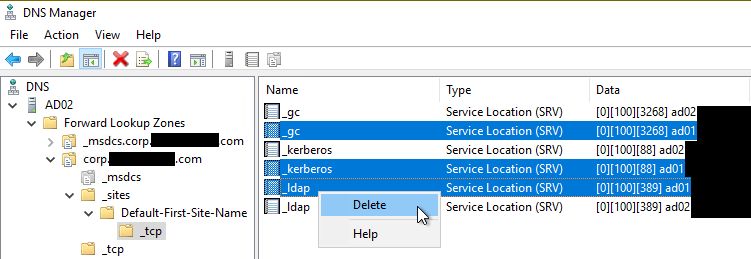
-
Under the _msdcs forward lookup zone, expand all folders, and their sub-folders, and delete any SRV records that point to the domain controller that was removed.